The Ip Address Specified For Communication Between This Forefront Tmg
Feb 9, 2013 - Rebooted the server and following alert did not show anymore: The IP address specified for communication between this Forefront TMG. For SSL communication, select the internal server certificate from the. Click Select IP Addresses and select Specified IP addresses on the Forefront TMG. Simplify Forefront TMG Migration By Web Chaining To An Upstream Proxy Microsoft Forefront TMG’s web filtering capabilities officially ended on 31 December 2015. However, a large portion of Forefront TMG users have not migrated to an alternative platform or are struggling to complete their migration.
Microsoft Forefront TMG’s web filtering capabilities on 31 December 2015. However, a large portion of Forefront TMG users have not migrated to an alternative platform or are struggling to complete their migration. This article will describe how to use Forefront TMG’s web chaining feature to use an upstream proxy to take over the web filtering duties until your migration is complete.
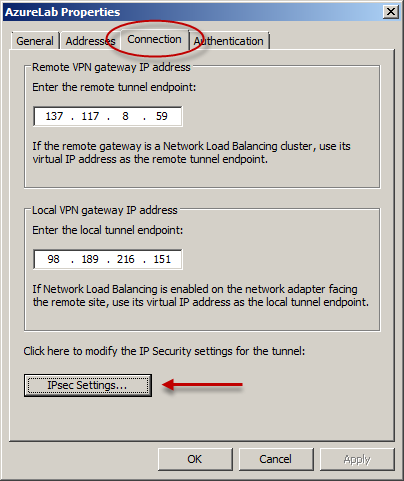
This assumes you have a replacement proxy server ready for use but you have not been able to migrate your user base yet. The problem with changing proxy serversIn most environments you need to explicitly define a proxy server to be used by internet accessing applications. In most cases, these are browsers such as Internet Explorer, Chrome and Firefox but there are many more.Java is a huge culprit for causing proxy server migration issues. Depending on the version you have installed, it may or may not cache proxy settings, it may or may not authenticate correctly, and it may or may not work. The same goes for other applications such as Skype and iTunes.Another concern for corporate environments are server services that require Internet access, such as WSUS (Windows Server Update Services), SCCM (System Center Configuration Manager), and Antivirus management servers that need to download and distribute virus definition updates. And then of course there are things like Linux servers that have been hard coded with the IP address of your old Forefront TMG server.Basically, if your migration plan is to simply rip and replace Forefront TMG with something else, you are going to have a hard time.
Simplifying Forefront TMG Migration With Web ChainingForefront TMG’s Web Chaining feature is normally used when you have a distributed environment where remote sites connect through a private WAN to your primary Internet break out. Placing a local proxy at each remote site allows you to secure and filter requests from that site before it hits the main corporate proxy. Forefront TMG refers to this as an upstream proxy.Here’s the really nice part. The upstream proxy does not have to be a Forefront TMG server. It can be a different type of proxy such as, or whatever proxy you intend to migrate to.
The proxies also do not have to be in separate networks – they can be right next to each other.Based on the specified rules on Forefront TMG, it will forward Internet requests to the upstream proxy, which then applies its own set of web filtering rules, before retrieving or denying the web request.The advantage here is you do not initially need to migrate all users, devices and servers to use your new proxy. This can be done gradually because Forefront TMG’s security is now reinforced by a web filtering and malware scanning proxy.Creating Your Forefront TMG Web Chaining RuleThe configuration below needs to point to your new proxy and match its settings as far as IP, ports and authentication is concerned. The upstream proxy also needs to allow the traffic through. It is advisable to configure the upstream proxy to do this before implementing the following. From the Forefront TMG management console, select Networking Web Chain. Click Create New Web Chain Rule from the Task Pane. Specify a name and click Next.
Add the External Network as a Destination and click Next. Select Redirect requests to a specified upstream server and click Next.
Specify the Server, Ports and optionally set a User Account. Click Next. The Backup action should be set to Ignore Requests. Click Next and Finish. Checking the Traffic flowYou will now be able to observe if the web traffic is being forwarded to the upstream proxy by running a Live Query in logs and reports and checking the destination IP address. This will no longer be the public IP address of the site, but instead, it will be your upstream proxy server.You should also see corresponding traffic on your upstream proxy. You will be able to distinguish it from clients connecting directly to your new proxy since the source for the web chained traffic will be the Forefront TMG server.
The same is true for the username if you specify one. It is not the users credential but rather the one specified by the web chain. Affects on logging and reportingAs mentioned above, all of the traffic from Forefront TMG will now be seen as a single user or a single device. This will not affect your logging and reporting from a TMG perspective. The image below still shows that traffic is being logged and reported on as if TMG is requesting the sites directly.However, as Forefront TMG’s Web Protection services is no longer in play, categories will not be logged, and productivity based reports, dashboards and alerts will no longer work.
For more information about what to do with TMG’s URL filtering and category-based rules, see our article:.Your new proxy on the other hand will not have insight into who the individual users are. This will only be visible for clients using the proxy directly and authenticating against the new proxy. Everything still going through Forefront TMG effectively becomes one user. Web Chaining LimitationsThe Web chaining feature can get you out of a bind if you’re still using it as a secure web gateway, but it does have some limitations. You can specify multiple chaining rules, but the flexibility of the rules aren’t great. You cannot for instance forward requests from a specific user but not another. The same limitation is true for the source.
You can be selective when it comes to the destination, but you will not be able to use URL categories due to. Suggested Upstream ProxiesFor many users, but there are many viable alternatives. As long as the replacement device supports standard explicit proxy connections, you should be able to use it as an upstream proxy. If you are currently using and would like to keep reporting continuity, we do have sister products for the popular Forefront TMG replacements, with. (for Sophos UTM). – generic log analysis supporting over 200 log file formats.
As you most probably know, Microsoft has discontinued Forefront Threat Management Gateway 2010 (TMG) without announcing an official successor. With no direct upgrade path being available from Microsoft, more and more loyal TMG users start looking around for a replacement.For a long time, many TMG users considered Microsoft Unified Access Gateway (UAG) as a replacement.

Whether or not UAG is a suitable replacement for TMG was subjects to debates all around the net. While the two products offered, in general, some of the same capabilities, there is no way UAG could replace Forefront TMG as a front-edge line of defense.
Besides, Microsoft was slowly backing out of the forefront security market by taking features away from UAG, clearly deprecating some features as of UAG SP3. Finally, it came to the logical end: Microsoft has announced it will not deliver any future full version releases of Forefront UAG, effectively discontinuing the product on July 1, 2014.Now is the perfect time to look around for a third-party alternative to Forefront TMG and UAG.
One of such alternatives is Sophos UTM. Sophos UTM as a TMG ReplacementSophos the company has been around for a long time as a developer of anti-virus products.
As of 2009, Sophos expanded its business by acquiring Astaro, the developer of Unified Threat Management (UTM) products. Apparently, they timed the market just perfectly.
With Microsoft discontinuing Forefront TMG, the now current Sophos UTM is seen as a perfect TMG replacement not only by TMG users but by Sophos itself. In fact, Sophos clearly positions its UTM solution as a replacement for TMG. In this article, we’ll have a look at firewalling and intrusion prevention features of Sophos UTM, as well as its other features essential for securing the edge of your network infrastructure. Sophos UTM: a Unified Threat Management SystemSo what is Sophos UTM? According to Sophos, the product offers complete protection for the entire network.
Sophos UTM offers a built-in firewall, IDS/IPS, forward and reverse authenticated proxy, anti-malware protection, and has applications to secure Wi-Fi, VPN, Web and email, the latter including spam protection. As you can see, this is a pretty extensive feature list. Let’s have a look at what this product can really do to secure your network, and whether it really is a viable replacement for Forefront TMG.
LicensingUnlike the original Forefront TMG and many of its alleged replacements, Sophos offers one of the most flexible licensing policies. If you settle with Sophos UTM, you can choose to license individual protection modules or buy one of the pre-packaged deals. With Sophos UTM, you can either assemble an all-in-one security system or configure just the bare basics depending on your needs and your budget. InstallationSophos offers multiple deployment options depending on your requirements. You can get a stand-alone hardware or virtual appliance with Sophos UTM pre-installed.
Alternatively, you can install Sophos UTM on a dedicated or virtual server (e.g. Hyper-V, VMWare or one of the many supported virtualization platforms). Since our goal is finding a replacement for software-based Microsoft Forefront TMG, we’ll try the software-based version of Sophos UTM.Sophos delivers the software-based UTM system as a bootable ISO disk image. If you were to deploy it on a dedicated server, you could burn the image on a physical DVD disc. In our case, we were installing Sophos UTM to a virtual server, so no physical blanc DVD is needed.To install Sophos UTM, we did the usual preparations, creating a new virtual machine in Hyper-V, attaching the ISO image supplied by Sophos and selecting is as a boot device. Booting the virtual machine opens the setup window.
The setup goes smooth and with no surprises. Sophos UTM will need to re-partition your disk. You will also need to choose between 32-bit and 64-bit kernels; we went with the 64-bit one. Wait till the setup finishes copying the files, and proceed to the actual configuration.After the setup has finished copying the files, you can configure the settings of the internal NIC by specifying its IP address, net mask and default gateway.
Finally, you will see the prompt telling you how to open the configuration settings (they are configured via a Web interface by accessing the link ). The server will then reboot. You will then have a couple more steps to complete the setup via the Web interface.At last screen, you’ll be specifying the hostname and location or the Sophos UTM server, administrator’s password and email address. You will have to accept the displayed Terms and Conditions and either upload your license file (specifying which features of Sophos UTM will be activate) or run the product in time-limited demo mode.
As you can see, in-place upgrades are supported at any time by simply uploading a new license file.The next steps of the wizard will help you configure the actual security system. You will specify the internal and external interfaces and choose the rule template that applies to internal users. By selecting the appropriate template you can restrict your internal users to Web only, allow or disallow instant messaging or peer-to-peer file exchange, and so on.Depending on your network configuration, you’ll need to specify which IPS policy templates should be loaded.
There are templates for securing various network components against specific types of attacks, e.g. As you will see, the user interface reminds that of a typical router or firewall appliance. This is only logical considering that you can get Sophos UTM as a stand-alone hardware appliance.
The user interface is highly consistent throughout the many configuration screens. This consistency makes interpreting data easy at first glance regardless of which screen you are looking at.The UI contains real-time charts for many types of logging and data. These real-time charts will come handy to both newcomers and seasoned administrators, presenting an overview of what’s happening around the network in a glance.
When it comes to usability, this user interface may even beat Forefront TMG.One thing to note about this user interface is the default logout time. You will be logged out automatically after 5 minutes of inactivity. This is a user-configurable setting, so you might want to change that to a longer period of time before configuring all the rules and settings. Sophos UTM: FunctionalityIn this part of the article, we’ll discuss the various functions of Sophos UTM such as routing and firewalling, authentication, proxying, VPN support, and some advanced features such as mail filtering, malware inspection and so on.FirewallingConfiguring the firewall does not differ much from doing such in Forefront TMG. The firewall is configured via the Web interface through firewall rules.To create a rule, one should specify one or several sources such as IP addresses, networks or user groups; specify protocols (objects) and destinations (which, again, can be an IP address, a network or a user group). You will then specify an Action to allow or disallow the activity. You can optionally specify the exact time period during which the activity is permitted or disallowed.While creating a new firewall rule, you’ll be selecting the options from a list pre-configured objects.
Of course, you have an option to create them just before selecting them. This, too, is similar to how TMG handles things.Shall you need to diagnose how a particular rule works, you can enable the “Log” option for that rule. This creates a log very similar to one produced by TMG.As you can see, firewalling in Sophos UTM looks deliberately similar to that in TMG so far. However, there are some new firewalling options named “Country blocking” and “ICMP” that were not available in TMG.
Country BlockingCountry blocking, as the name suggests, is used to block all traffic originated from certain countries or entire continents based on the information returned by GeoIP. Forefront TMG did not have such an option, although experienced administrators could be able to create an advanced rule to perform a similar task. Country blocking comes handy when you want to enforce your security policy, improve malware protection and URL filtering.
ICMP ControlICMP options are used to control ICMP traffic on a per-packet basis. The firewall can be configured to perform a certain action based on the packet properties, e.g. By responding to traffic, forwarding it transparently or simply ignoring it.
This enables you to control which information you make available to the world. A common use for this type of rules is hiding the firewall from network probes such as ping, lookup and traceroute.
RoutingSophos UTM offers static, policy-based and dynamic (OSPF and BGP) routing. IPv6 support is available for all routing options, although it is configured via a separate menu.One thing missing in Sophos UTM compared to Forefront TMG is RIP. This, however, is compensated by TMG’s lack of support for dynamic routing. Static RoutingConfiguring a static route is unsurprisingly straightforward. You’ll be configuring which network or which object is reachable through which interface of net-hop gateway or object, and set a metric, if one’s required.An interesting feature of Sophos UTM is the ability to create blackhole routes to discard certain types of traffic instead of routing it to the final destination. This comes handy when you want to discard certain types of traffic before it reaches the firewall engine, which can save a lot of CPU cycles under heavy load. Policy-Based RoutingConfiguring policy-based routing is done similar to configuring static routing.
You’ll be specifying which traffic is forwarded to which destination based on the source network, protocol, destination network and the interface the packet arrived on, and then configuring a static route for that particular type of traffic using the same objects. Dynamic RoutingDynamic routing (OSPF) is enabled via the first menu page. However, before activating dynamic routing, you’ll need to configure at least one area first. You’ll be setting area ID and type, authentication type, and cost.
You’ll also be setting the forwarding interface and any virtual links that might be active in the area. You can optionally determine which routes are to be redistributed and whether or not the system should advertise a static default route.Now when you configured the area, you can return to the first menu page and enable OSPF routing.BGP routing is configured in a similar fashion. Before enabling BGP routing, you’ll need to configure at least one neighbour by setting the name, IP address, AS number and authentication type. You can optionally specify things such as filter and route maps.Talking of route maps and filter lists, both will require you to enter a name and determination method (either an IP address or an AS number) to determine the applicable traffic type. You’ll need to specify networks that are subjects to the filter or map. On the next configuration step, you’ll need to configure metric, weight, preference and AS prepend function for the route map. The filter list is much simple to configure, as it will only require you to select an applicable action (allow or block).
NATSophos UTM functions as a NAT gateway, translating public IP addresses to private addresses on the internal network. Sophos UTM offers two modes of operations: dynamic (Masquerade) and static (NAT). You can create masquerading rules by specifying the internal network to masquerade, selecting the external network interface, and defining the external IP address to use.You can create the following types of NAT rules:.
Source Network Address Translation (SNAT). Destination Network Address Translation (DNAT). Full NAT combining SNAT and DNAT. 1:1 NAT mapping the IP addresses of the entire network to another network in 1:1 mode. No NATA feature worth a special mention is the “No NAT” option. This feature allows VPN traffic pass through without being subjected to a dynamic NAT rule.Another interesting feature is the ability to automatically generate firewall rules matching your NAT rules.
Protocol Independent Multicast Routing with IGMP SnoopingSophos UTM supports Protocol Independent Multicast routing with full IGMP snooping. To configure, you’ll need to select an interface, specify IGMP versions to allow, configure a Rendezvous Point and PIM-SM routes. All this allows manipulating the flow of multicast traffic.
BridgingFinally, Sophos UTM can act as a bridge. In this mode, Sophos UTM functions as a switch. It supports STP and offers the option to forward ARP broadcasts, becoming fully transparent from a layer 3 perspective and allowing for basic filtering to occur on a lower level. For this, you’ll be configuring firewall policies on layer 2 objects.
AuthenticationWhile Sophos UTM supports authentication via Active Directory, and supports LDAP, Novell eDirectory, RADIUS and TACACS+ authentication servers, the system offers a very innovative approach to authentication. In Sophos UTM, authentication is a strict username to IP matching scenario. There are no “users” in traditional sense. In Sophos UTM, users exist as regular IP objects, just like networks and hosts.This authentication model has some interesting consequences. On the positive side, Sophos UTM can substitute a user group everywhere you’d normally need to configure a network. This in turn allows making all the features role-based, giving administrators endless possibilities.To give an example, you can configure the firewall policy to not just allow certain users accessing an internal network. You could, for example, dynamically create static routes to networks based on user credentials, bypassing the firewall for extra speed.
Or you could build a specific firewalling policy just for one user to allow for comprehensive policing.Why don’t others use similar authentication schemes? There is a downside, too. When configuring firewall rules, you’ll have to consider the effects of this authentication scheme. If, for example, you need to configure access to an internal code repository to all members of the Developers group when they are connecting from the staff subnet.
The Ip Address Specified For Communication Between This Forefront Tmg Services
In TMG, this would be as simple as creating a rule allowing traffic to the code repository from the staff subnet, and then specifying the Developers user group. In Sophos UTM, you’ll be creating a rule that denies access to that code repository to all networks except the staff subnet, and adding a rule that allows members of the Developers group to access it. This will make the firewall discard all traffic to code repository except when originated from the staff subnet. The rule will process the traffic from the staff subnet, only allowing IP addresses assigned to the members of the Developers group.As you can see, with this authentication scheme you can do some amazing things. However, configuring some scenarios can be not just as easy and straightforward as in TMG.
Authentication ProvidersOn a technical side, Sophos UTM supports Active Directory, eDirectory, LDAP, RADIUS, and TACACS+ as authentication sources. Configuring authentication mostly consists of configuring the server IP addresses, ports, and other settings specific to the authentication provider of your choice.Sophos UTM offers a fallback scheme, allowing you to configure which other authentication providers to use and in what order should the primary provider fail.Configuring each authentication provider is pretty straightforward. There are just some things to mention that aren’t often encountered in similar products. When troubleshooting authentication issues, Sophos UTM has a feature shared among all authentication providers. This option allows checking the user’s authentication credentials against your authentication provider’s database to see whether the user with given credentials exists, and if it does, to which groups the user belongs.As far as authentication methods go, Sophos UTM looks very similar to Forefront TMG.
If offers all the familiar methods including No Authentication, Proxy Authentication, and Client Authentication (via Sophos Authentication Agent, which acts in a similar way to TMG Firewall Client).There are no surprises here, just a few things to mention. In Sophos UTM, Proxy Authentication works in both standard and transparent deployments.
This is a bit unusual, as we’re used to see transparent proxying breaking authentication. The transparent proxy allows for Agent (via Sophos Authentication Agent) and Browser authentication.Browser authentication presents users a Web-based logon, allowing them type their authentication credential in a browser window.
This is an easy way to do it, the downside being that it’s limited to Web browser traffic.Sophos Authentication Agent is another authentication option. It can be manually distributed as an.EXE or.MSI file, pushed via a Group Policy, or distributed with whatever method used on your network.On initial setup on a client, Sophos Authentication Agent asks the user to provide their authentication credential, giving an option to store them for fully transparent access to protected resources in the future. This option provides a truly transparent, single sign-on operation for the user regardless of logon/logoff state of their computer.ProxyingSophos UTM comes with a forward and reverse proxy. The difference here with TMG in that the forward proxy is not configured explicitly. Instead, proxying is configured via Web Filtering, while proxy authentication is configured in Authentication section.Other than that, there are little surprises to be found in Sophos UTM proxying. It is interesting to note that, while Sophos UTM offers the caching feature in the web filtering configuration, it does not provide an option to control cache size, threshold or other properties.
The proxy can be configured to exclude certain URLs or URL patterns from filtering options, which includes caching.Sophos UTM offers policy based proxying via configurable Web Filtering Profiles. This option allows administrators defining multiple Web filter behaviour profiles based on the trust mode of the content (Trusted, Neutral, Unverified or Suspicious). This allows selecting traffic based on certain characteristics, and determining an action to perform on such traffic depending on set rules.SSL proxying is also available. As already noted in the Authentication chapter, Sophos UTM offers SSL filtering in a transparent setup, allowing to scan traffic transferred over the end-to-end tunnel. This is performed by eavesdropping on the SNI to determine to tunnel endpoint, which in turn allows Sophos UTM to redirect SSL traffic to the proxy and perform content inspection transparently.
For this to work, the client will need to trust the CA certificate on the UTM; a public signing certificate works great for this purpose. Reverse ProxyingIf you were looking for a reverse proxy and were unable to find it, you are not alone. Sophos named the feature “Webserver Protection”. Other than the name change, the feature does pretty much what you’d expect of a good old reverse proxy.Configuring reverse proxying is pretty straightforward. One thing to mention is the lack of authentication in the reverse proxy. Sophos UTM offers no options to enforce user based access in Webserver Protection controls. This does not seem to follow the logic of the rest of the setup.
The reason for this is the company’s working on combining their SSL VPN solution with reverse proxy, which should enable authentication of incoming users. Another feature expected in the new setup is the return of forms based logon that was popular in TMG.
This functionality is not yet available as of today though. VPNSophos UTM offers comprehensive support for all the VPN options available on the market. The system supports IPSEC, HTML5-based, L2TP, PPTP, SSL, and Cisco client-based remote user VPNs.
In addition, Amazon VPC, IPSEC, and SSL based site-to-site tunnels are supported.IPSEC site-to-site VPN is one of the more popular VPN options. Configuring such VPN is as straightforward as it ever could be. The configuration setup reminds of a similar procedure in a Cisco ASA, which is to say it will look familiar to anyone who had set up a VPN before, so we won’t talk much about it except the few innovative features. Strict Routing and TMG CompatibilityOne interesting option here is named “strict routing”. When enabled, this option makes the system create policy-based routes instead of using the available static routes. The difference between this mode and normal operations is quite amazing. In normal mode, Sophos UTM routes all traffic destined for the tunnelled subnet through the tunnel.
If the “strict routing” option is enabled, Sophos UTM will only forward packets matching both the source and destination subnets through that tunnel. As you can see, this mode can potentially save quite a lot of bandwidth by discarding traffic that was not destined through the tunnel in the first place. On a side note, this “strict routing” mode is pretty much the standard mode of operation for every other VPN gateway except for TMG, so the “normal” mode can be rather seen as “TMG compatibility” mode. Site to Site VPNOne interesting feature available to Sophos UTM users is the ability to create site-to-site SSL VPN tunnels. Obviously, this requires the use of Sophos UTM on both sides of the tunnel (server and client), but if you are going Sophos all the way, you’ll appreciate how easy it handles the tunnelling.To create a site-to-site VPN, you’ll need to set up one UTM as a server and another one as a client. The client UTM will initiate a VPN connection automatically when it needs to transfer traffic to the server.Configuring a VPN in this scenario is easy.
You’ll need to set the primary UTM as a server and specify local and remote subnet objects, and the UTM will generate a downloadable package for the remote UTM to import. The package will contain all the necessary settings as well as the secure certificate. As you can see, there is no need to manually configure anything on the client UTM; a very smart approach if you ask me.
SSL VPN SettingsSophos UTM offers all the commonly available settings you could expect from an SSL VPN. You can configure connection encryption, hashing, and all the other settings. Traffic compression and NAT network options are also available for tunnelled traffic. Remote Client VPNConfiguring a remote client SSL VPN is just as easy. Drag and drop is supported for adding or removing authorized users and groups that are allowed to connect over SSL VPN.
The setup automation goes as far as to offering to download the SSL VPN client on the user portal for the authorized users or groups.Configuring PPTP and L2TP access is even easier, as here you will only need to specify authorized users and determine the address assignment and a VPN pool, if applicable.Configuring IPSEC client VPN is a bit more complicated. Its setup is similar to the way you configure site-to-site IPSEC tunnels, so you’ll be configuring the policies and bind them to Connection Profiles. Similar to SSL client VPN, authorized users will be offered to download an executable file to configure access on their side.Configuring a Cisco IPSEC client VPN tunnel is a lot simpler, and not more difficult than setting up the SSL client VPN. HTML 5 VPN PortalThe ability to create HTML 5 VPN portals is extremely interesting. Essentially, HTML 5 VPN portals enable users to create easily create VPN tunnels securing communications between their device and their corporate network. As this is pure HTML, these VPN tunnels can be created easily from any device running any type of operating system as long as it has a Web browser supporting HTTPS/SSL.
This includes Windows, Linux, Mac OS X, Android, iOS, and many other platforms.For the end user, HTML 5 VPN tunnels are super convenient. It does not require ActiveX, Java or a downloadable client to use. The entire configuration works via an HTML page loaded in a Web browser.
There is even no need to log in every time, as resource credentials can be stored on the device for automated login.How does this look in reality? In Sophos, HTML 5 VPN portal enables you to add client-server style applications and HTTPS Web sites to the user portal.
These will be presented as icons to the user. When launched, these applications (or Web sites) will be securely tunnelled through an SSL connection. The idea is similar to Cisco webVPN, which also requires no software or hardware client to operate.While this idea looks great on paper, there are two major limitations restricting the usefulness of HTML 5 VPN tunnels. First, the choice of supported applications is currently limited to RDP, HTTP/HTTPS, SSH, Telnet and VNC.
Second, there is no single sign-on available.In reality, these limitations make many Sophos customers to only offering clientless RDP/SSH/Telnet sessions to remote users. The absence of a single sign-on limits the convenience of offering multiple applications in a user portal, and although there is an option to present a preconfigured username and password to the published backend servers, this is at best a workaround.
In our view, HTML 5 VPN Portal, while a nice feature, is still at its infancy until Sophos integrates true authentication support in their reverse proxy. Traffic Inspection and FilteringIn this chapter, we’ll talk about the many inspection and filtering options available in Sophos UTM. Web FilteringSophos offers a decently comprehensive set of filtering options for all types of traffic. The filtering of Web traffic is managed through the Web Filtering configuration menu. In this menu, you can configure general Web filtering, Web filtering profiles, and end-user URL filtering parameters.We have already described the basics of Web Filtering Since in one of the previous chapters, so let’s now talk about URL filtering, which is available under the “URL filtering” tab.
URL FilteringThe URL content filtering helps administrators determine which content is allowed on their network, and what the users are not allowed to access. Sophos UTM allows you to either blacklist or whitelist content by default, allowing you to either allow all types of content that do not match the filtering rules, or block all content that does not make it through the white list.As a basic anti-virus protection, Sophos URL filtering allows you to block Web sites containing spyware, malware and botnets. This filter is rather basic, and works based on the list of known spyware sites.
There is an additional parameter called “Block URLs based on reputation”. This one is slightly more interesting as it bases its decisions on a McAfee database combined with data obtained from the Sophos’ own reputation system.
When this option is enabled, UTM will block URLs with reputation levels lower than the configured reputation (Trusted, Neutral, Unverified and Suspicious). This is similar to how Forefront TMG used to work; however, Sophos opted to disable this option by default, enabling old-school black/white list filtering as default behavior.The next parameter allow blocking or enabling Web sites that belong to certain categories such as Entertainment, Games, Job Search, Nudity, etc. Finally, there is an option to block (or allow) URLs that don’t belong to any of the above categories. Note that you can add or delete categories and add or remove sites to categories by using the URL Categories tab.Configuring exceptions is easy with lists available on the right side of the window. Administrators can specify URLs that will be always blocked, as well as URLs that will be always allowed. Finally, there is an option to specify users or user groups who are allowed to bypass blocking.For search engines, there are options to enable Safe Search on Google, Bing and Yahoo.
In addition, you can enable YouTube for Schools if you have a valid YouTube for Schools ID.Web Filtering ProfilesWeb Filtering profiles extend basic URL filtering by enabling administrators maintain separate a set of filters for certain users or networks. This system only allows using a network object as a source once. As a result, configuring, for example, a profile taking care of traffic for “Internal” effectively disables general filtering for traffic originating from this network. No other Web Filtering profiles will apply to “Internal” traffic as well. This sounds unusual, and may confuse administrators who are new to Sophos; however, this system is only logical considering the overall Sophos authentication model.How does this work in reality?
Let’s say you have a privileged group of users named “Executive Staff”. This group needs access to Web sites that other employees are not allowed to access. One option would be configuring an override, but let’s say the executives don’t want to be bugged, requiring plain, unrestricted access to these resources.In this scenario, an administrator would need to set up the general filtering to drop all the appropriate categories for sessions from the internal network, and create a web filtering profile that drops all those categories with the exception made for the privileged users. For all this to work, you’ll need to configure the user group “Executive Staff” as the source network for the profile.
You will also need to configure the privileged user’s workstation by installing the Sophos Authentication Agent or a proxy on the privileged user’s computer. Malware InspectionAs any forefront protection system these days, Sophos offers a malware inspection option. Sophos offers the choice of two anti-virus engines, allowing the users to choose between its own proprietary engine or two engines. If the uses opts to use two anti-virus engines, the system makes use of Avira in addition to Sophos. Administrators have options to remove malicious content such as harmful JS code or other embedded content, and block content by file extension or by MIME type.The option to block large downloads by specifying the maximum file size threshold is also configured here. Finally, there is an option to log accessed and blocked pages.Enabling SSL inspection in Sophos is as easy as checking the “Inspect SSL” checkbox and uploading a trusted signing certificate. Alternatively, UTM’s signing certificate can be distributed to the end users.Sophos offers a range of options for configuring exceptions to the policy.
Administrators can configure exceptions by disabling any combination of components of the anti-malware and URL filtering including Authentication, Caching, Antivirus, Extension blocking, MIME blocking, URL filtering, Content Removal, SSL scanning, Certificate trust, Certificate date and logging options. All these options can be either disabled permanently or based on a match criteria such as source, URL pattern, user group or destination URL category.Interestingly, these criteria can be nested with logical AND and OR operators, allowing some fine-tuning of the exceptions. The limitation here is the ability to use only one type of match statement on every step of the rule.In Sophos, exceptions are extremely flexible. For example, you can exclude streaming content from scanning, enable or disable SSL inspection, determine which protocols are eligible for proxy processing (by default FTP, HTTP, HTTPS, HTTP Proxy, LDAP), whether to block encrypted objects and objects that cannot be scanned, and so on, and so forth. Intrusion ProtectionSophos UTM provides a real-time intrusion protection system (IPS). Sophos IPS scans network traffic in real time, looking for known signatures and analyzing for suspect behavior. The IPS component can either drop suspect traffic silently or terminate the connection.Advanced configuration options include the ability to specify which attack patterns to look for and determining which actions to take depending on each category.
DoS Attack ProtectionDoS attack protection is also available via IPS. The DoS protection module can be configured to identify excessive traffic on TCP, UDP and ICMP protocols, and thrashing such traffic according to the preset threshold. In addition, port scanning protection is available using the same metering as the DoS protection module (it watches for cumulative sessions and ports per IP instead of the number of packets per second though). Port scanning protection allows administrators to drop, reject or log identified port scanning attempts.Needless to say, exceptions can be created for the IPS and DoS protection components.
Mail Filtering and Spam ProtectionSophos comes with a highly sophisticated anti-spam system. The spam protection supports POP3 and SMTP modes, and covers everything from mail relaying to message routing. Quarantine control is implemented for end users.Configuring POP3 protection is similar to Web Filtering.
There are malware protection options with the choice of Sophos or Sophos + Avira engines, the option to reject messages exceeding a certain size, and the ability to create exceptions.In SMTP mode, Sophos spam protection works as an SMTP relay for mail flow within the organization. This mode is quite comprehensive, enabling full control over the entire mail flow within your organization from simple white, black and grey-listing to advanced domain and site routing profiles.The malware protection function scans SMTP traffic in transit, dropping infected messages before they even reach the main engine. Potentially harmful messages can be quarantined or discarded. There is also an option of adding a custom footer to all scanned messages.The implementation of mail quarantine in Sophos is quite advanced, allowing the end users to release quarantined messages. This option, of course, is only available to those users who are allowed to release their own email. When configured, this greatly reduces the load on system administrators while allowing messages identified as false positive matches to pass through.The actual spam filtering configuration is similar to configuring malware protection. There are options to drop spam messages in transit (there are different options for confirmed and suspected spam), thus reducing the load on the UTM.
There is an option to maintain a Real-Time Blacklist, allowing administrators configuring extra RBL zones. The default configuration in Sophos uses the controversial Spamhaus database; the ability to override some of its rules is a welcome addition for any system administrator.Suspected spam can be passed through with or without a warning message, added to quarantine or discarded. The same options are available for confirmed spam.Administrators have the ability to add certain address patterns and expression lists as spam detection rules. Finally, there are options for Reverse DNS lookups, greylisting, bounce tag address validation and SPF checks.Does it come as a surprise that Sophos implemented the ability to override any of these settings for any particular address, network or user group?
Administrators can configure flexible exceptions by specifying which filters should be skipped based on a maximum of three statements (source host/network, sender address or recipient address) linked by the OR operator (there is no AND available here).In SMTP mode, Sophos can be configured to scan outgoing messages as well, applying the same policies and exceptions as for incoming mail. Application FilteringSophos UTM recognizes traffic belonging to certain applications, allowing administrators apply traffic filtering rules based on application instead of simple protocols. By enabling this feature, administrators can configure pretty much everything from firewall rules to proxy configuration and routing.In Sophos, application support is administered via Sophos’ own AppAccuracy program. This program consists of a huge database of applications. As of this writing, the database contains more than 10,000 entries corresponding to different applications. Interestingly, this database is dynamically maintained: information about new applications is automatically (and anonymously) uploaded by all participating Sophos UTM devices.Administrators can create application rules overriding all other configuration settings, thus enabling administrators to block or allow traffic based on the application.
This, for example, allows enabling Skype messaging but disabling Skype VoIP calls. Or allowing social media per se but disabling streaming videos. The possibilities are pretty much unlimited. QoSSophos’ implementation of QoS supports can work as a straight QoS with traffic marking, classification and processing, and serve as a means of traffic shaping and policing.QoS can be enabled for ingress and egress interfaces. You should enable QoS on both interfaces in order to allow any packet operation. The QoS configuration is divided into two parts.
The first part allows configuring the traffic selector, allowing to determine which traffic to look for. The second part of the interface allows configuring the bandwidth pool used to apply traffic shaping and policing to matching traffic.Configuring the traffic selector is easy. You can either set Sophos UTM to listen to incoming DSCP values (if upstream marking is configured) or specify traffic based on parameters such as source, protocol, application and destination. There is also a configurable threshold allowing the policies to kick in only after the identified types of traffic reach a certain amount of transferred data (in KB).Configuring the bandwidth pool is even more straightforward. You can specify the minimum amount of bandwidth that should be available for each type of traffic. In addition, you can specify the maximum, effectively throttling certain types of traffic (like streaming videos, for example).The possibilities of traffic Sophos shaping in combination with application control are quite amazing.
You can reserve a certain amount of bandwidth to critical applications such as VoIP, and, at the same time, limit the amount of bandwidth available to some less important stuff like social networking or YouTube videos without banning them completely. User PortalSophos offers a neat feature called User Portal. The user portal enables administrators to allow certain administrative activities to end users. This, for example, allows users to manage quarantined mail, deploy authentication agent or import the SSL filtering root certificate without asking administrators.User portals are enabled under the Management menu by specifying which networks are allowed. From there, you can configure which components are allowed. High AvailabilityFor demanding applications requiring near 100 per cent uptime, Sophos UTM offers high availability support in both active/active (“Cluster”) and active/passive failover (“Hot Standby”).
The type of available failover depends on the installed license. In addition, Sophos offers interface high availability by supporting upstream link redundancy and interface teaming.Sophos offers automated and manual configuration modes for hot-standby and cluster operations. In automatic mode, deploying hot-standby is the easiest among all similar systems. The administrator will need to specify a Sync (heartbeat) interface. After that, all connected UTMs will automatically elect a master based on uptime, synchronize their operations and monitor uptime. If downtime is detected on the master, one of the other UTMs will take over its operation.The only restriction here is that you cannot mix hardware and virtual appliances, or different models of hardware UTM. In other words, all UTMs need to be of the same versions.In manual configuration, administrators can configure both stand-by and cluster setups.
In this mode, the preferred master can be manually specified as well as the fallback interface. Other settings include automatic configuration of slave devices, the handling of system upgrades etc.A word on system upgrades: Sophos offers an option to update all UTMs at the same time or one by one, which helps prevent a system outage should an update cause downtime or break your system configuration.
Link RedundancyIn Sophos, link redundancy is available as Uplink Balancing and Link Aggregation.Uplink Balancing allows combining multiple physical uplinks (they could be of the same or different ISP) and address them as if they were a single logical entity. Static (with a control protocol) and dynamic (802.3AD LACP) aggregation is supported. In dynamic mode, the system can dynamically monitor interfaces, adding or removing connections and distributing the load across the adjoining switches and other hardware.The advantage of using dynamic uplink balancing is that you are not only creating redundancy, but can also distribute load across the interfaces, thus increasing overall system performance if all interfaces are properly working.The obvious downside, however, is that you are forced to connect all the interfaces to the same logical entity.
This makes it unusable with Layer 3 and higher redundancy operations.Sophos works around this problem by making use of Uplink balancing. In this mode, the UTM will monitor service availability on the primary link and automatically switches to a secondary link should it detect an availability issue. In these cases, Sophos UTM will automatically adjust all related NAT and routing operations.You can utilize multiple uplinks at the same time through Sophos Multipath Routing.
In this mode, you can specify what traffic will be balanced between the primary and secondary uplinks based on source, service and destination. Reporting and MonitoringSophos offers reasonable monitoring and includes some basic reporting capabilities. The support for SNMP based monitoring is included. Sophos UTM allows configuring traps for just about any action from logon events to IPS alerts and DoS attacks.Administrators can specify what events are to be seen by the administrator, whether to simply log the event, alert the administrator with an email or raise an SNMP alert.A daily summary is available, containing pretty much the same basic information you can find in Forefront TMG reports.
This includes load, bandwidth, top 10 users, 10 protocols, websites and so on.While the level of detail available in Sophos reports matches that of Forefront TMG, extending its reporting capabilities with a third-party solution such as can really improve administrators’ experience, make it one of the best tools on the market.PricingSophos has a complex, if not complicated licensing system. Sophos UTM features are licensed separately from the appliances. Sophos pre-packaged some popular configurations, making it possible to purchase packages such as base system or full guard. Notably, the virtual appliances require separate user licenses, while the physical appliances don’t.Sophos can be licensed on 1, 3 or 5-year terms. Support is included with all licenses, while extended support is available through Sophos partners.
It is the partners who are responsible for e.g. The replacement of physical appliances.There is no point in listing all the prices, so let’s just have a look on how it compares with Forefront TMG. Price Comparison: Sophos vs. TMGComparing the pricing between Sophos and Forefront TMG is less than straightforward.
With Sophos, you are licensing the entire physical (or virtual) appliance that does not need a separate Windows license. With Forefront TMG, you are licensing the Windows Server installation plus the TMG installation, which increases the cost of ownership. If you add extended support, you’ll be paying for both products in the case of Microsoft, and for a single product with Sophos.To make things even more complicated, various contract options affect pricing severely in Microsoft Forefront TMG deployment.On the other hand, Sophos has an extremely complicated licensing scheme that only its authorized resellers can fully master. You’ll be paying a fee for each user license, but only in the case of a virtual appliance. If you are licensing a physical appliance, there are no separate user licensing required.We tried to compare three configurations covering typical mid-size network configurations, then averaged the price. As a result, Sophos UTM averaged some 1.4 times more expensive compared to a similarly configured Forefront TMG system.
VerdictSo can Sophos UTM replace Forefront TMG after all? In our opinion, it is fully able to do so, albeit at a higher price compared to TMG.Sophos’ strong points are the authentication model, the Web interface and general configuration amount, the routing engine, the many filtering and protection options and the depths of configuration possible.
Some other options are nice but haven’t reached the complete refinement yet, such as the clientless HTML 5 VPN with limited application support or the nesting of the Web filtering profiles. Reporting could benefit from a third-party add-on (e.g., here it is article which describes how to setup Sophos UTM to work with ProxyInspector - ).There are some misses, too. The reverse proxy not including authentication support is one example, no support for unequal load balancing is another.We mentioned the licensing already, so here we go again: Sophos licensing model is complicated to the point of being impossible to understand for a mere mortal.
Figuring out the total cost of our desired configuration required a contact with experienced professionals, and yet three different (albeit close) quotes were received.The decision to make the virtual appliances almost as expensive as the physical appliances (and even more expensive in some cases where a large amount of user licenses is required) raises questions.With Sophos UTM being approximately 40 per cent more expensive than Forefront TMG for our sample configuration, the pricing is definitely raising questions. It’s probably not a surprise that a system like that is more expensive than a comparable TMG deployment, but we are surprised to see it’s that much more expensive. ConclusionPricing and minor issues aside, we were generally pleased while we were using Sophos UTM. It was easy to set up and configure and a pleasure to use.
Sophos UTM comes as close to replacing Forefront TMG as we’ve seen so far. Should it ever receive a good reverse proxy with authentication, it would become a functional copy of TMG with major improvements.If you decide to go for Sophos, go for it! Here at ADVSoft, we give our full support to this system, making ProxyInspector fully compatible with all versions of Sophos UTM. Information on how to configure ProxyInspector to process Sophos logs is available atTags:,.